Living in the modern globalized business environment, data leakage is not only a concern to the individual but has become a significant danger to businesses both large and small. Once sensitive data of your company is released (customer records, internal credentials, financials, source code) the impact can spread into the reputation of the company, legal responsibility and regulatory measures.
The positive news: it is possible to proactively determine whether a leakage took place.
The first step to deep scans is to observe the red flags:
- Begin by Survey Your Perceptible Signals.
- Drastic rises of targeted phishing attacks under your company name.
- Unknown logins, particularly the ones that do not have a reason or justification.
- Public leaked credentials in either a public or dark-web forum.
These are the indicators that your information may be in the air, although you may not have received all the evidence.
- Quick Scan with Public “Breach Check” Tools.
A few free services are useful in checking whether your emails or domains used in business have been in known leaks. For example:
- Have I Been Pwned (HIBP) – allows you to check the email address or domain disclosures.
- F-Secure Identity Theft Checker and Mozilla Monitor are other sources of verification.
They are a good start, however, do not forget: they are mostly consumer-driven, not enterprise-scale breach detection.
- Transfer to Enterprise-level checkups and Dark-Web Checkups
There are a lot of leaks that will not be represented in the open databases, this is why it is necessary to monitor it with business in mind. This includes:
- Follow forums and markets in the dark-web where your company name or domain is mentioned.
- Verifying leakage of source-codes, credential-stuffing logs and employee password dumps.
- Tracking exposures of shadow IT – forgotten servers, dormant accounts, project archives.
In recent study, 16 billion+ leaked credentials were identified circulating in the internet-based world, which is even indicative of the sheer size of the exposure world.
- Perform Internal Audits and Cross Check Logs.
Internal audits are important, even with the outside help.
- Look at access logs of the review to detect anomalies in the administration or database logins.
- Detect and delete the orphaned accounts of the old employees.
- Patch or discontinue old systems which may cause leakage.
Guidelines on Data breach response published by the FTC advise auditing the people who had access during the compromise and implementing stricter access policies as soon as possible.
- One Leak Finds a Way out, Move Systematically.
After confirming exposure (tool alert, log anomaly, dark-web find):
- Establish the extent – what, who, why.
- Isolate the breach – remake credentials, de-authorize access, put outbound vulnerable endpoints.
- Inform the stakeholders- customers, partners and regulators where needed.
- Investigate root cause – human error, vendor compromise or malware?
- Enhance the protection measures, enforce multi-factor authentication ( MFA ), least-privileged access, and monitoring.
Note all the actions down, as it becomes necessary to comply and prevent in the future.
- Develop an ongoing Observation Psychology.
Leaks of data do not occur once in a lifetime. The threat actors keep on changing with infostealer malware, phishing, and credential-stuffing attacks.
To stay protected:
- Add domain + email monitoring to dark-web intelligence.
- Install, deploy access anomaly detection tools.
- Conduct frequent employee security training.
- The only defense that can be maintained is vigilance.
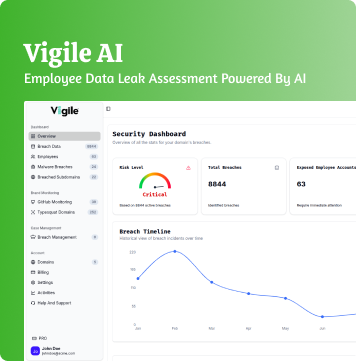
Why Vigile Can Turn You into a Leader.
Vigile is a leak detection and response enterprise-grade vendor. We actively keep scanning of the dark web, breach databases and credit credential exposures to provide you with real time warnings whenever your company data is at risk.
The difference with Vigile is that you do not only respond to any leaks, but you identify them, contain them, and fix them, before they turn into headlines.
Ready to take control?
Go to the Vigile.ai to understand how Vigile can be used to identify the presence of data leaks in your company before they can do any harm.