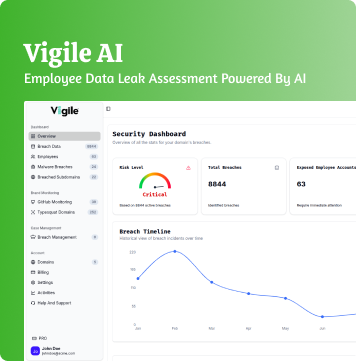
From Alerts to Action: Turning Security Signals into Decisions
Introduction The contemporary security systems are very efficient in detecting activity- however, detection in itself…
Security Fatigue Is Real, Here’s How Automation Helps
Introduction The current cybersecurity teams are working in a 24/7 threat environment. Wareings are 24/7, systems are…
Ways to Secure Remote Teams against Credential Leaks and Infostealers
Remote work and hybrid work have changed the way business is conducted in a certain…
Dark Web Myths Every Business Leader Should Stop Believing
The dark web sounds like a movie story or hackers playground and this is the…
How Hackers Find Your Employees’ Passwords in Minutes (and How to Stop Them)
A single weak password is all that is required to get an entire organization brought…
The Hidden Cost of Ignoring Leaked Credentials
Regarding cybersecurity, most organizations are concerned with the protection of their perimeter but are unaware of…
Why Employee Breach Monitoring Should Be Part of Your Cybersecurity Strategy
In today’s digital-first world, employees are both an organization’s greatest asset and its biggest vulnerability.…
What Really Happens After a Credential Leak: The 5 Stages of a Breach
No company is afraid of the term credential leak. Or what does happen when your…
What Hackers Do with Your Leaked Credentials (And How to Stop Them)
If you think a leaked password is “no big deal”, think again. In the underground economy of…
How Often Should You Check the Dark Web for Your Company’s Credentials?
If you’ve ever asked yourself, “How often should we scan the dark web for our company’s credentials?”, congratulations, you’re already ahead…