While most of us spend our digital lives on Google, LinkedIn, or Slack, there’s another side of the internet that never shows up in search results — the dark web.
It’s a hidden network where stolen data, login credentials, and confidential company information are traded like currency. For cybercriminals, your employees’ leaked passwords could be their easiest entry point into your systems.
According to IBM’s Cost of a Data Breach Report 2025, over 40% of breaches began with compromised credentials. That means if your team’s emails or passwords are leaked, your company could already be exposed — without even knowing it.
🚨 Why Your Company’s Credentials Might Already Be on the Dark Web
Every time an employee signs up for a tool, joins a webinar, or reuses their corporate password on another site, there’s risk.
When those third-party platforms are breached, their databases often end up dumped or sold on underground dark web forums.
These stolen credentials are then used by attackers in credential stuffing or phishing campaigns to infiltrate corporate networks.
Here’s how it usually happens:
- A third-party platform is hacked.
- Your employee’s corporate email and password are exposed.
- The credentials are sold or traded on dark web marketplaces.
- Hackers use automated tools to try the same credentials on your email, VPN, or cloud systems.
If even one match works — game over.
🧠 How to Check If Your Credentials Are on the Dark Web
Finding out if your data is being sold isn’t as simple as a Google search. The dark web is intentionally unindexed, anonymous, and dangerous to browse directly.
But there are safe and legal ways to monitor it.
1. Use a Dark Web Monitoring Tool
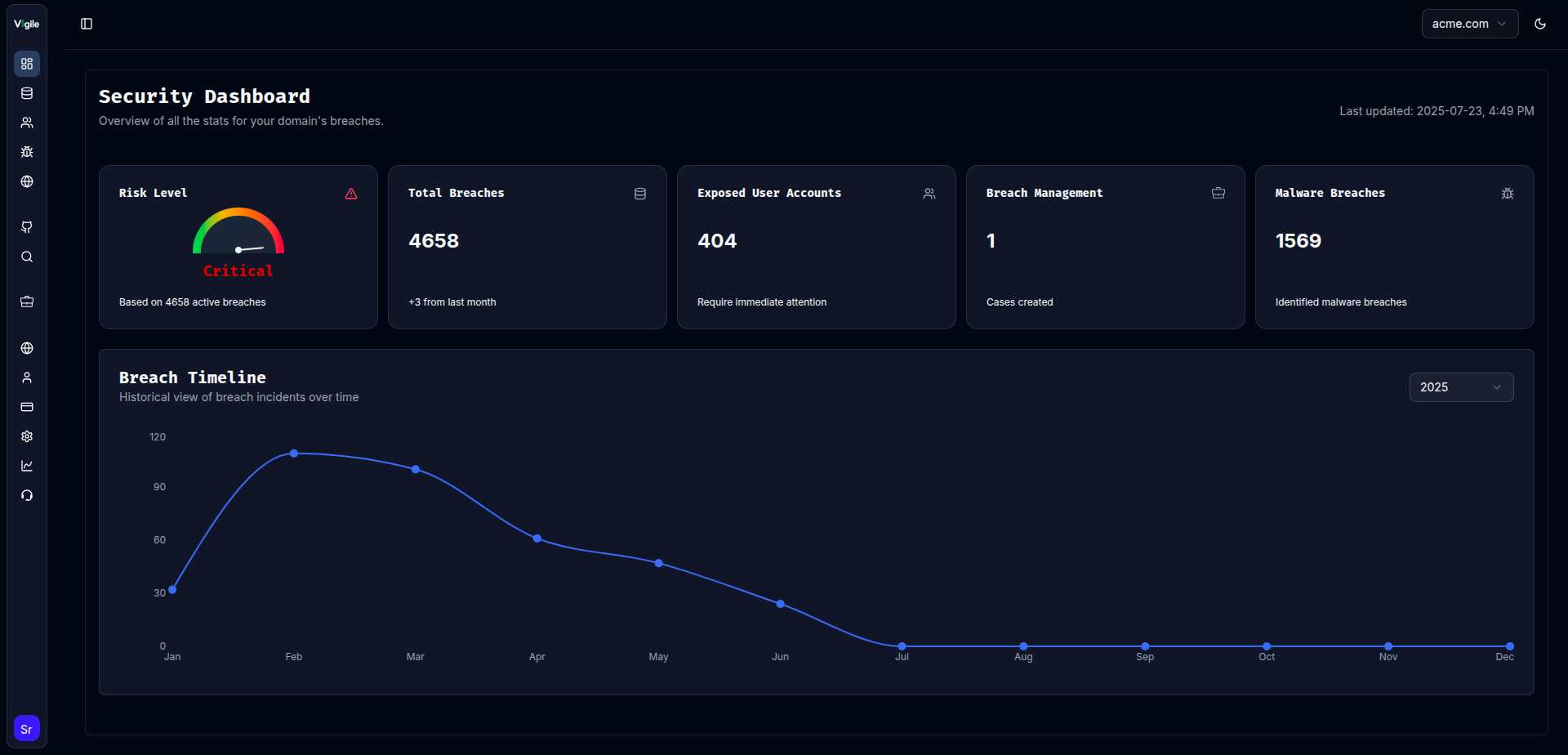
AI-powered tools like Vigile.AI continuously scan dark web sources, underground forums, and data dumps to identify exposed credentials linked to your company’s domain.
Unlike public breach checkers, these tools provide real-time alerts the moment new leaks appear.
2. Monitor Corporate Domains
Always keep an eye on your company’s primary domains (like @yourcompany.com).
If any email addresses connected to that domain appear in dark web listings, it’s a clear sign your data is compromised.
3. Check for Password Reuse
Attackers rely heavily on password reuse. Conduct internal audits to ensure employees aren’t using identical passwords across platforms.
Encourage the use of password managers and multi-factor authentication (MFA).
4. Leverage Threat Intelligence Reports
Regularly review dark web intelligence reports that highlight credential leaks related to your industry.
This helps your security team understand emerging attack patterns and take preventive action.
🧩 What to Do If You Discover Leaked Credentials
If you find out your company’s credentials are circulating on the dark web, don’t panic, but act fast.
- Immediately change all affected passwords.
- Force logouts and reauthentication across corporate accounts.
- Enable MFA (Multi-Factor Authentication) for every critical system.
- Investigate login patterns for suspicious access attempts.
- Start continuous monitoring to catch future leaks early.
The faster you act, the less damage attackers can cause.
⚙️ How Vigile.AI Helps You Stay Ahead of Dark Web Threats
At Vigile.AI, we believe prevention starts with visibility.
Our AI-powered dark web and credential monitoring platform continuously scans millions of sources — from dark web marketplaces to leaked data repositories — to detect exposed credentials before hackers exploit them.
With real-time alerts, breach intelligence, and automated risk scoring, you’ll know exactly which accounts are compromised, when, and how to respond.
🚀 Protect Your Organization Before Hackers Strike
Don’t wait to find out your data is for sale after the damage is done.
Start monitoring your company’s credentials today with Vigile.AI — and stay one step ahead of every breach.