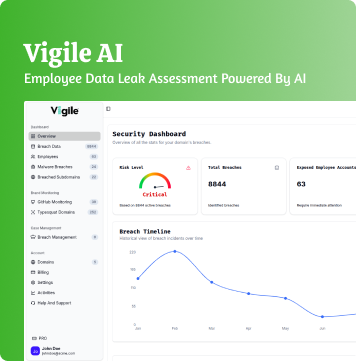
Every business leader dreads it; waking up to find their company’s data floating around on some hidden marketplace in the dark corners of the internet. The dark web is a hidden part of the internet where hackers and cybercriminals buy, sell, and trade stolen data; from usernames and passwords to full corporate databases. The truth is that dark web credential leaks happen far more often than most companies realize. What’s scarier? Many businesses don’t realize their data has been exposed until it’s too late.
So, how can you tell if your sensitive data is already out there? Let’s break down the top 10 signs your company’s credentials may already be on the dark web.
1. Employees Suddenly Locked Out of Accounts
When legitimate users get unexpected “password incorrect” messages or lose access altogether, it’s a strong indicator that stolen passwords are being used by someone else. Attackers often change credentials immediately after gaining access, cutting off legitimate users.
2. Suspicious Login Attempts from Unknown Locations
If your logs show multiple failed logins attempts or successful logins from unfamiliar countries, time zones, or IP addresses, it’s time to investigate. Attackers often test compromised accounts using automated tools across thousands of systems until they hit one that works.
3. Your Domain Appears in Public Breach Databases
Tools like Have I Been Pwned or commercial dark web monitors reveal if your email domain has appeared in a data breach. When your domain shows up, there’s strong chance dark web credentials connected to your company are being shared or sold privately.
4.Sudden Surge in Spam or Phishing Emails
An unexpected flood of targeted phishing messages often means attackers already know some of your internal data. They use this information like employee names, departments, or even internal lingo to craft believable messages that trick staff into giving away more information.
5. Increase in Multi-Factor Authentication (MFA) Prompts
If employees start getting MFA prompts, they didn’t initiate, it’s a huge red flag. It usually means someone is trying to log in using stolen passwords, and the second authentication step is blocking them. Treat these alerts as attempted breaches, not technical glitches.
6. Password Reuse Across Business and Personal Accounts
It’s human nature to reuse passwords, but this creates massive risk. If an employee’s password is leaked from a social media or e-commerce site, and they use the same one for work, you suddenly have a data leak sign leading directly into your internal systems.
7. Unusual System or API Activity
A sudden increase in failed API requests, or connections from unfamiliar endpoints, could mean attackers are testing stolen credentials against your APIs. This kind of stealthy probing often goes unnoticed until deeper breaches occur.
8. Unknown Devices Accessing Corporate Apps
Unrecognized mobile phones or devices logging into email, Slack, or cloud storage can signal that your credentials have been compromised. Attackers often add new devices to authenticated sessions to maintain silent access even after password resets.
9. Mentions of Your Company on Dark Web Forums
Cyber threat intelligence tools sometimes detect your company’s name, domain, or internal assets being discussed on hacker forums. Even a single mention can mean your dark web credentials or sensitive data are already circulating and someone is planning to use them.
10. Vendors or Clients Reporting Suspicious Activity
Cybersecurity doesn’t end at your firewall. If customers notice phishing attempts, invoice scams, or unusual communications coming from your domain, that’s often a downstream symptom of compromised accounts within your environment.
What You Should Do Next
If any of these warning signs sound familiar, don’t panic; act fast:
- Enable real-time breach monitoring to catch exposures early.
- Rotate all high-risk passwords and enforce strong password policies.
- Implement MFA everywhere possible.
- Educate employees about phishing and credential hygiene.
- Schedule regular penetration testing and vulnerability assessments to identify weak points before attackers exploit them.
Don’t Wait for a Breach to Go Public
In today’s digital world, assuming your credentials are safe is a dangerous gamble. Proactive security is no longer optional it’s essential.
That’s where Vigile.AI comes in.
At Vigile.AI, we help organizations detect, monitor, and protect their digital assets before cybercriminals strike. Our intelligent dark web monitoring and proactive security solutions empower businesses to stay ahead of potential threats.
Don’t wait for your credentials to surface on the dark web. Protect your company today with Vigile.AI’s proactive cybersecurity solutions and keep your data and reputation secure.